Access Futon Over SSH to Administer CouchDB
Traducciones al EspañolEstamos traduciendo nuestros guías y tutoriales al Español. Es posible que usted esté viendo una traducción generada automáticamente. Estamos trabajando con traductores profesionales para verificar las traducciones de nuestro sitio web. Este proyecto es un trabajo en curso.
Futon is a web-based administrative interface for Apache CouchDB. You can use SSH to connect to your Linode’s CouchDB server and then access Futon securely through your web browser. This quick answer assumes you already have CouchDB running on your Linode.



Establish an SSH connection
SSH with Windows Using PuTTY
If you need to get set up with PuTTY, see our guide on using it and verifying your Linode’s SSH key fingerprint.
To set up the SSH tunnel:
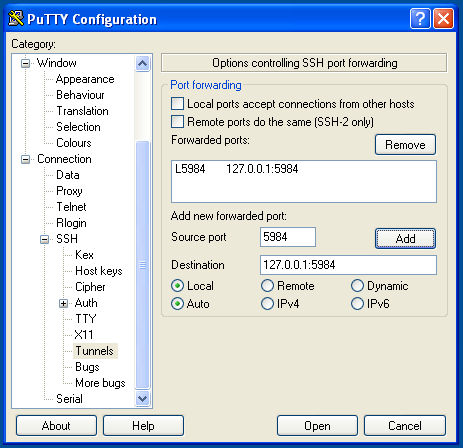
- In PuTTY’s configuration window, go to the Connection category.
- Go to SSH, then Tunnels.
- Enter 5984 in the Source Port field and 127.0.0.1:5984 in the Destination field.
- Click Add, then click Open to log in.
SSH with Mac OS X or Linux
Enter the following into the terminal of your local computer:
ssh -L5984:127.0.0.1:5984 user@your_Linode's_IP
Access Futon from a Web Browser
Once the SSH connection is established, open a web browser on your local computer and go to http://localhost:5984/_utils/. You’ll see the Futon overview page and despite it being an http URL, you’re actually connecting to your server securely through an SSH tunnel.
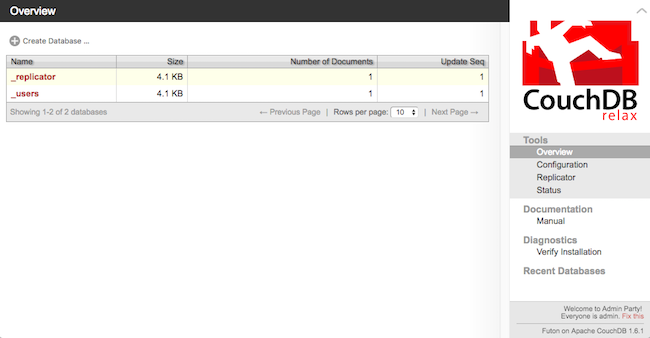
http://localhost:5984 without needing to access the server over a public IP.More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
This page was originally published on

